5 minutes
SCADAsploit module: Modbus Scan
Let’s get to know SCADAsploit a little better starting from one of the auxiliary modules present: Modbus Scan.
Position ourselves in the folder where we installed SCADAsploit and start it using the command $ ./scadasploit.py. Following the same approach philosophy of Metasploit, we can search for all modules that contain a keyword using the search <keyword> command or display the complete list of modules present with the show modules command.
In our case we will use search modbus to identify the SCADAsploit modules that can help us during our pentesting work on a Modbus TCP network.
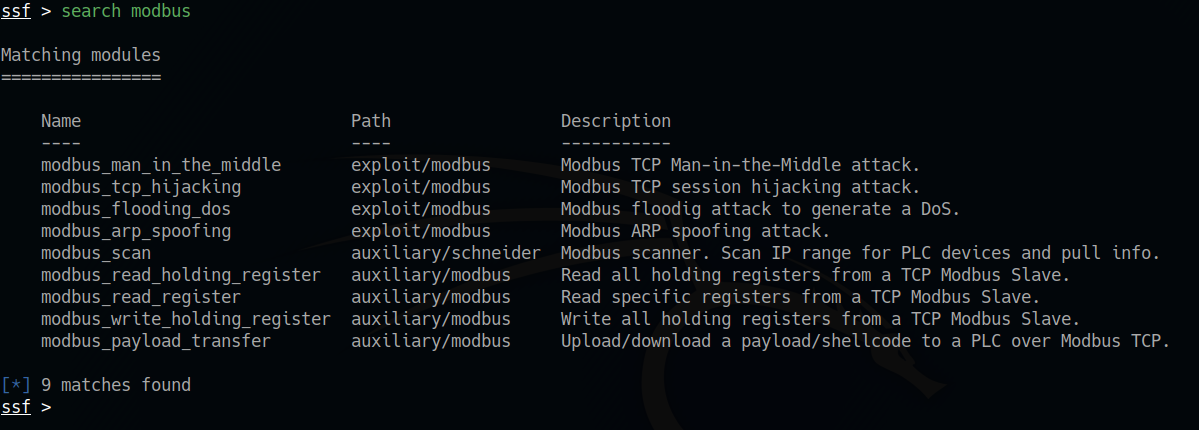
The list includes both auxiliary modules and exploits, which can be recognized via the “Path” column. For our first test we decide to scan a Modbus TCP network, so we select the Modbus Scan module via the use auxiliary/schneider/modbus_scan command and display the list of parameters via the show options . As we can see, the module belongs to the “auxiliary” category.
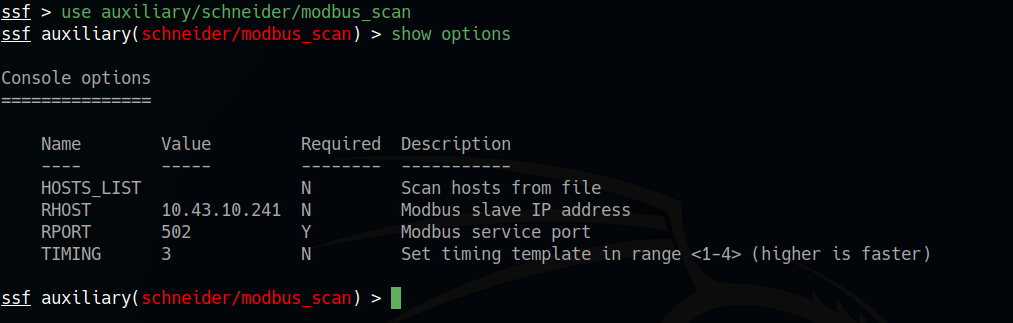
Modbus Scan is a module for scanning devices connected to a Modbus TCP network. It can be used to scan all devices for information about the communication card, firmware version, MAC address.
Network scanning can be done by specifying the IP address of a single device or a range of addresses using the CIDR notation (eg 10.43.10.0/23). Alternatively, it is possible to enter the name of a text file which contains the list of IP addresses of the hosts, following a simple format which specifies the address and any non-standard port.
10.43.10.100
10.40.11.58:5020
10.0.1.1/24
In our case we scan a single device.
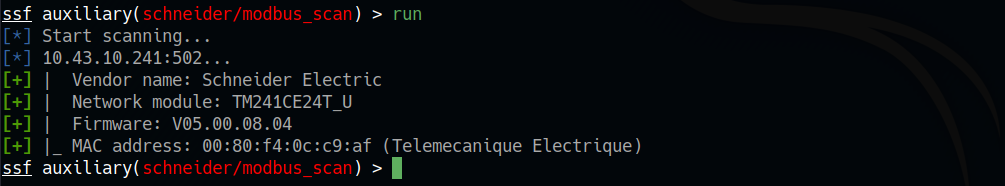
And here in a moment we are able to recognize our device, the version of the firmware installed and the MAC address, all useful information for a subsequent exploit action.
Schneider Modicon PLC and UMAS
Schneider Modicon series PLCs programmed with UnityPro and based on Unity OS starting from version 2.6 use the UMAS protocol. This is a kernel-level protocol that also has an administrative level of control.
The UMAS structure exploits that of Modbus and is a derivative of the old Xway protocol used since the first series of Telemechanique PLCs. The main feature is that it uses the 90 (0x5a) function code of the Modbus protocol to send and receive a much richer set of information. The packaging of the payload is little-endian, which may seem strange since Modbus is big-endian.
The UMAS packet begins with a 16-bit field specifying a “UMAS Function Subcode”, followed by a variable number of bytes making up the payload.
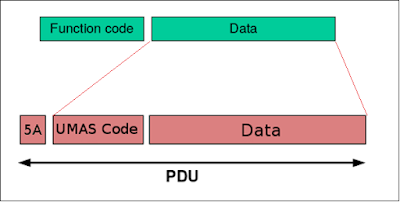
Therefore, UMAS requests have a structure of this type:
[TCP Packet] [Modbus Header] [5A] [UMAS CODE (16 bit)] [UMAS PAYLOAD (Variable)]
Instead, all the answers follow this pattern:
[TCP Packet] [Modbus Header] [5A] [RETURN CODE (16 bit)] [UMAS PAYLOAD (Variable)]
0x01 0xFE - OK
0x01 0xFD - Error
When a Schneider PLC receives a Modbus packet, it checks if the function code is 0x5A and, if so, uses some specific libraries to manage the UMAS extension. There are several “UMAS codes” able to perform many operations on the PLC, here are some of them:
| UMAS code | Function | Description |
|---|---|---|
| 0x01 | INIT_COMM | Initialize a UMAS communication |
| 0x02 | READ_ID | Request a PLC ID |
| 0x03 | READ_PROJECT_INFO | Read Project Information |
| 0x04 | READ_PLC_INFO | Get internal PLC Info |
| 0x06 | READ_CARD_INFO | Get internal PLC SD-Card Info |
| 0x0A | REPEAT | Sends back data sent to PLC (used for synchronization) |
| 0x10 | TAKE_PLC_RESERVATION | Assign an owner to the PLC |
| 0x11 | RELEASE_PLC_RESERVATION | Release the reservation of a PLC |
| 0x12 | KEEP_ALIVE | Keep alive message |
| 0x20 | READ_MEMORY_BLOCK | Read a memory block of the PLC |
| 0x22 | READ_VARIABLES | Read system bits, system words and strategy variables |
| 0x23 | WRITE_VARIABLES | Write system bits, system words and strategy variables |
| 0x24 | READ_COILS_REGISTERS | Read coils and holding registers from PLC |
| 0x25 | WRITE_COILS_REGISTERS | Write coils and holding registers into PLC |
| 0x30 | INITIALIZE_UPLOAD | Initialize strategy upload (copy from PC to PLC) |
| 0x31 | UPLOAD_BLOCK | Upload a strategy block to the PLC |
| 0x32 | END_STRATEGY_UPLOAD | Finish strategy upload |
| 0x33 | INITIALIZE_DOWNLOAD | Initialize strategy download (copy from PLC to PC) |
| 0x34 | DOWNLOAD_BLOCK | Download a strategy block from the PLC |
| 0x35 | END_STRATEGY_DOWNLOAD | Finish strategy download |
| 0x39 | READ_ETH_MASTER_DATA | Read Ethernet master data |
| 0x40 | START_PLC | Starts the PLC |
| 0x41 | STOP_PLC | Stops the PLC |
| 0x50 | MONITOR_PLC | Monitors variables, systems bits and words |
| 0x58 | CHECK_PLC | Check PLC connection status |
| 0x60 | SET_BREAKPOINT | Set a breakpoint on a specified rung |
| 0x70 | READ_IO_OBJECT | Read IO Object |
| 0x71 | WRITE_IO_OBJECT | Write IO Object |
| 0x73 | GET_STATUS_MODULE | Get status module |
Modbus Scan by SCADAploit
SCADAploit Modbus Scan module supports the UMAS extension and this allows us to retrieve more details when dealing with a PLC programmed with UnityPro, such as eg. the name of the CPU module, the memory card model and some data about the project file that has been loaded.
The nature of the Modbus protocol which does not require any authentication facilitates the gathering of information.
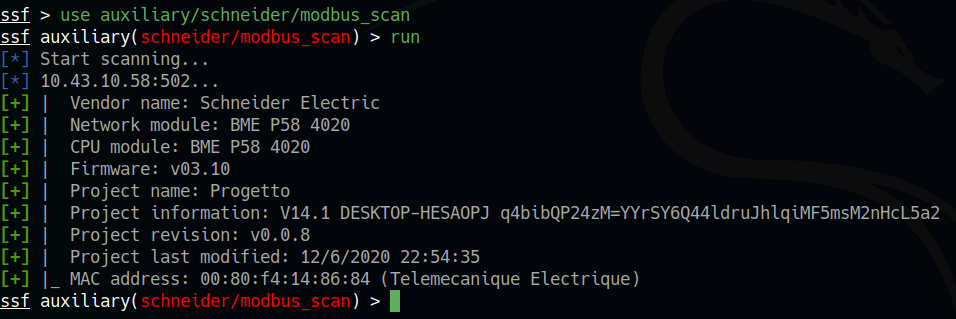
As we can see, in addition to the standard data we are able to collect important details about the project as well. By giving a practical example of how to use this information, the date of the last modification lets us understand how long the PLC has been in operation without software maintenance interventions. This may mean that it may be exposed to known vulnerabilities discovered at a later date that may not have been addressed.
Important note
This article is intended for educational and informational purposes only. Any unauthorized action towards any control system present on a public or private network is illegal! The information contained in this and other articles are intended to make people understand how necessary it is to improve defense systems, and not to provide tools for attacking them. Violating a computer system is punishable by law and can cause serious damage to property and people, especially when it comes to ICS. All the tests that are illustrated in the tutorials have been carried out in isolated, safe, or manufacturer-authorized laboratories.
Stay safe, stay free.