2 minutes
SCADAsploit Framework
This section is dedicated to SCADAsploit, a framework I’m working on dedicated to OT/ICS penetration testing. You ask yourself: “But isn’t Metasploit already doing this?”. Certain! So what is the need to create a new tool like this? I try to give some answers:
- framework exclusively dedicated to vulnerabilities of SCADA, PLC and other ICS devices
- written in Python, both the core of the framework and the modules
- “Metasploit like” interface
- greater focus on the installed PLC fleet, especially in Europe.
I don’t know if these points are sufficient to give greater meaning to the project, for me it was. I wanted to collect in a single environment the scripts that are commonly used during pentests in automation, and by chance I intercepted Sploitkit.
Metasploit currently has almost 70 modules dedicated to ICS systems, but most of them are for devices practically non-existent on the Italian market. If we consider the number of PLCs installed in Italy over the last 20 years, we find that Siemens + Schneider Electric are the masters with almost 2/3 of the market shares. Follow Rockwell Automation (formerly Allen-Bradley), GE, Omron especially on machine tools, some Phoenix and Wago and then a few others.
Hence the idea of SCADAsploit was born, a database of auxiliary modules and exploits dedicated to the main manufacturers and communication protocols, which facilitates the pentest phases. Using Python probably makes it more accessible for educational purposes as well.
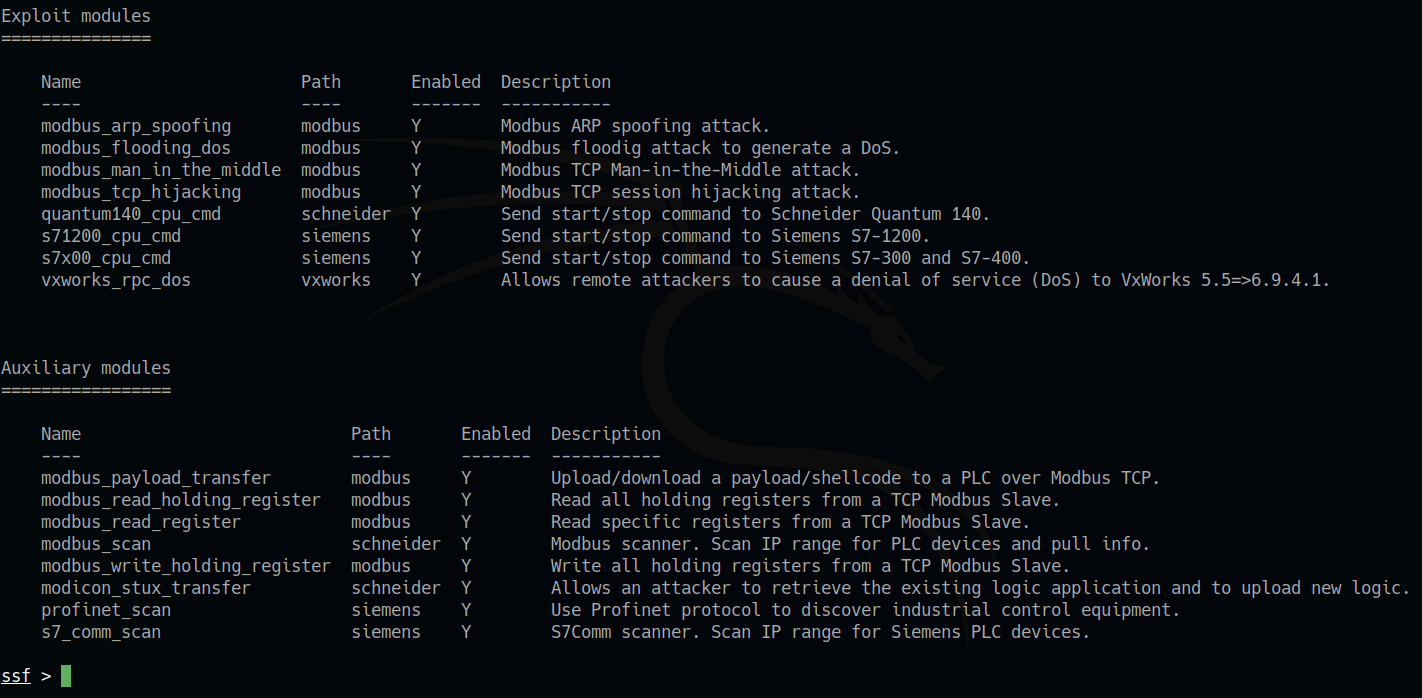
Main modules currently present
Following the same approach philosophy of Metasploit, also in SCADAsploit we find two categories of modules: auxiliary, exploit and commands. Auxiliary modules are dedicated to reconnaissance, scanning, data reading/writing operations, etc., while exploits base their behavior on exploiting a vulnerability.
In both categories we find a further subdivision according to the different PLC manufacturers.