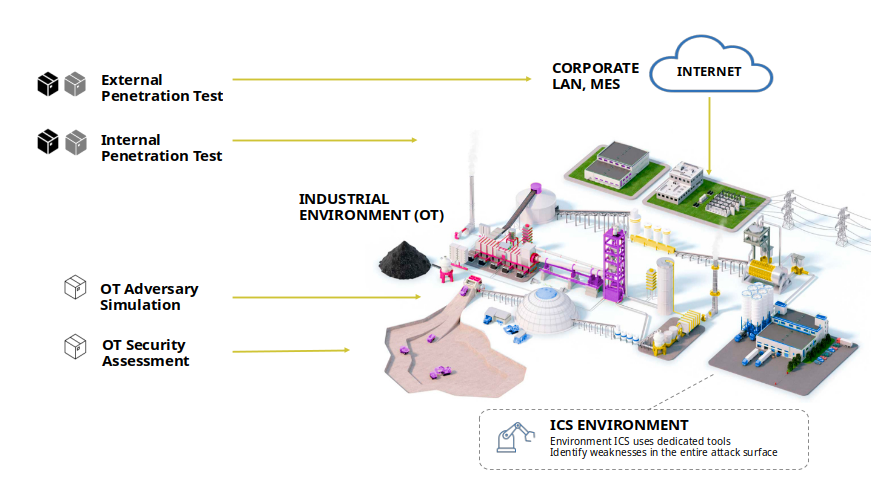
Empower your Red Team with cutting-edge Adversary Simulation Tool for OT Environments!
In today’s interconnected world, OT systems are the backbone of critical infrastructures such as power plants, manufacturing facilities, and transportation networks. However, their unique security challenges demand a specialized approach. With SCADAsploit, you gain a powerful ally in identifying vulnerabilities and fortifying the defenses of your OT environment.
SCADAsploit C2.OT can emulate different stages of an attacker killchain, and provide exploitation modules to help the SOC to validate the attacks and improve the internal defensive mechanisms. SCADAsploit is a pre and post-exploitation tool, providing auxiliary, exploitation and remote command modules to discover, evaluate and exploit an OT infrastructure.
Why SCADAsploit?
SCADAsploit C2.OT is your key to unlocking the full potential of OT/ICS security testing. It’s not just a tool; it’s a game-changing framework that empowers you to:
- Have access to a full Command & Control framework with distributed architecture.
- Execute pre and post-exploitation operations seamlessly.
- Evade AV and EDR systems, with advanced pivoting techniques reaching remote SCADA and PLC systems.
- Utilize a wide range of specialized auxiliary and exploitation modules for SCADA, PLC, and I-IoT systems.
- The ability to compromise IT infrastructures with stageless and staged beacons, with the most sophisticated obfuscation and evasion techniques.
- Control it all effortlessly through a potent Remote Client, enabling smooth server and module interaction with just a simple click.
It’s time to elevate your OT/ICS security game. Experience our Adversary Simulation and Penetration Testing framework in the IT/OT/ICS domain.
Comprehensive OT-Focused Testing
SCADAsploit goes beyond traditional cybersecurity tools by providing a dedicated suite of features tailored to the intricacies of OT networks. It mimics real-world attacks, allowing you to identify weaknesses and uncover potential entry points with pinpoint accuracy.
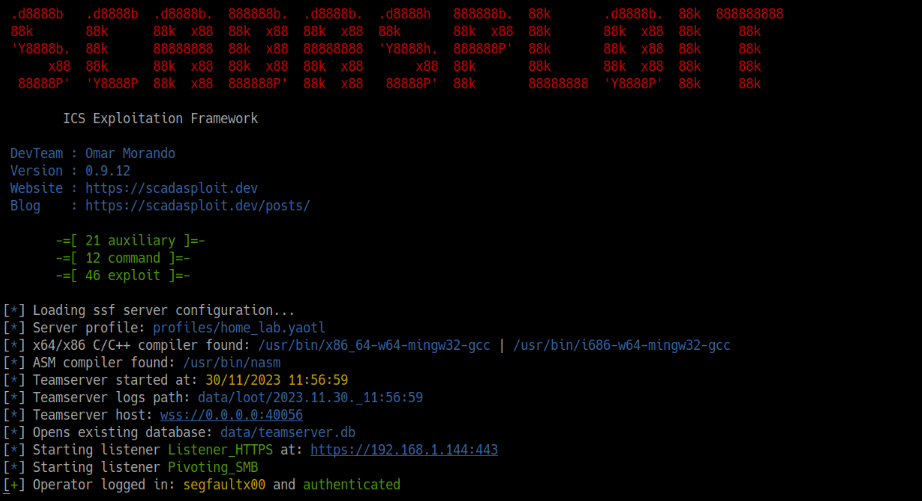
Flexible and Powerful Architecture
-
Client/Server Architecture: SCADAsploit boasts a robust client/server architecture that ensures seamless communication and collaboration between your team members. This scalable framework enables efficient distribution of tasks and enhances your offensive capabilities, allowing you to penetrate even the most complex OT environments.
-
Secure Client Connections: we prioritize the utmost security in SCADAsploit, providing you with the option to connect through industry-leading encryption protocols. Choose between Wireguard or Blu5 SElink, both renowned for their military-grade encryption capabilities, capable of communicating even with very little bandwidth available.
-
Beacon (Injector Agent): the beacon can be used in both a stageless and staged version to incorporate advanced evasion tricks, anti-debugging measures, and anti-sandboxing capabilities. It offers a range of process injection techniques and allows users to choose between WinAPI, NTAPI, and Indirect Syscalls. It also supports multiple pivot options, including SMB, TCP, WMI, WinRM, and the management of remote services via RPC.
-
External C2: the SMB and TCP variants of the beacon enable the creation of custom External C2 channels, allowing communication through legitimate websites like Slack, Discord, Microsoft Teams, and more, enhancing evasion capabilities.
Control and Remote PC Access
SCADAsploit offers a versatile client that allows comprehensive control over server functions. With our client, you have the power to access and manage the server’s features seamlessly. Our tool enables remote access to target PCs through a long list of commands or a terminal shell, providing you with the flexibility to execute commands and perform actions directly on remote machines.
Moreover, SCADAsploit facilitates the upload of new modules and payloads to the server, empowering you to expand your offensive capabilities. Stay one step ahead by constantly updating your arsenal and executing remote commands effortlessly.
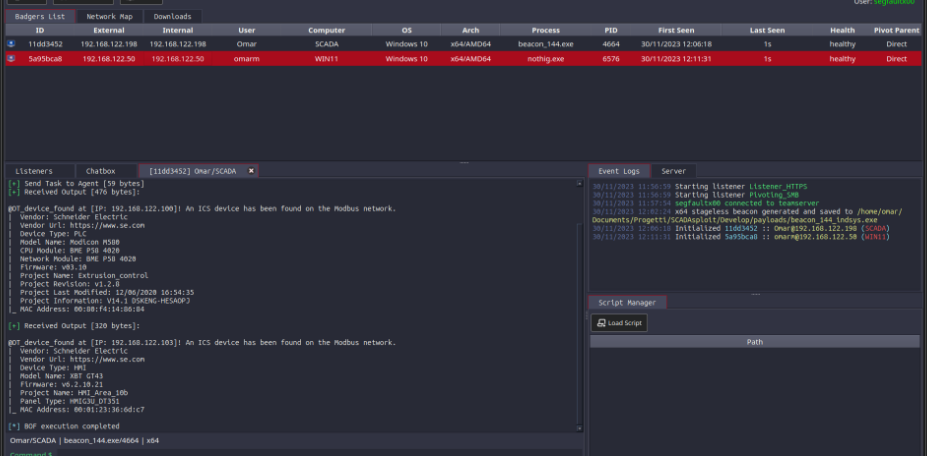
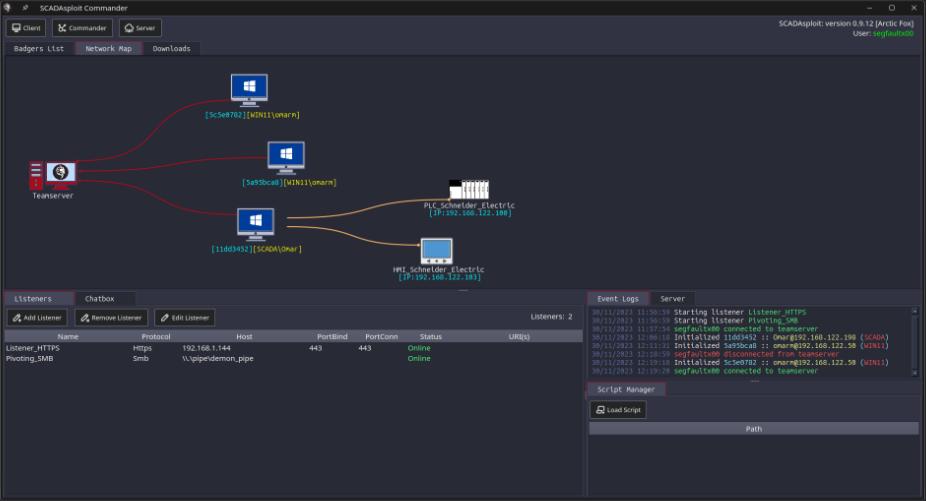
Asset Discovery, Network Mapping and Pivoting
Gain a comprehensive understanding of your target infrastructure with SCADAsploit’s asset inventory feature. It provides you with a detailed map of the network and identifies potential attack routes. This invaluable information empowers you to strategize and execute targeted offensive operations, maximizing the impact while minimizing risk.
SCADAsploit offers sophisticated techniques for lateral movement, starting from the compromised machine and reaching the connected SCADA and PLC systems.
Stageless and Staged Beacon
The beacon can be used in both as stageless and staged version to incorporate advanced evasion techniques, anti-debugging measures, and anti-sandboxing capabilities. The beacon offers a range of process injection capabilities and allows users to choose between WinAPI, NTAPI, Indirect Syscalls. It also supports multiple pivot options, including SMB, TCP, WMI, WinRM, and the management of remote services via RPC.
The beacon can be generated as Windows Exe, DLL or Windows Shellcode, whose payload can be encrypted with AES algorithm with QueueUserAPC, NativeAPI, Direct Syscall and Process Injection.
The SMB and TCP variants of the beacon enable the creation of custom External C2 channels, allowing communication through legitimate websites like Slack, Discord, Microsoft Teams, and more, enhancing evasion capabilities.