4 minutes
Hacking: Stuxnet-like attack on a Modicon PLC
Airbus CyberSecurity researchers recently demonstrated that hackers could launch an attack in Stuxnet-style against Schneider Electric’s Modicon programmable logic controllers (PLCs), but it is believed that products from other vendors could also be vulnerable to the same type of attack.
How does it work
The infamous malware Stuxnet, which the United States and Israel used to damage the nuclear program Iranian, was designed to target the SIMATIC S7-300 and S7-400 PLCs manufactured by Siemens. Stuxnet uploaded malicious code to targeted PLCs by abusing Siemens’ STEP7 software, which the German industrial giant supplied to program the controllers.
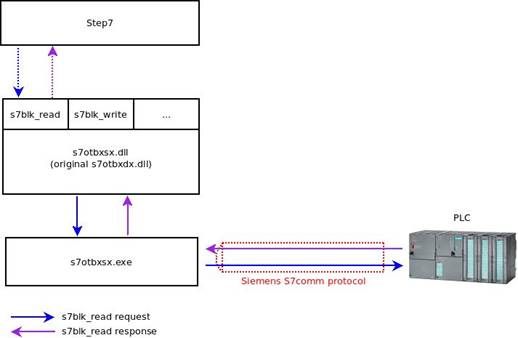
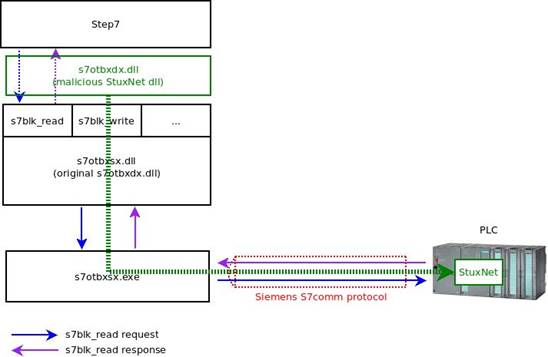
As I described in the previous article, Stuxnet replaced a library named s7otbxdx.dll, which STEP7 uses to access a PLC, with a malicious version using a method called “reflective DLL loading”. This technique involves renaming the concerned DLL (e.g. asmArm.dll) with another name (e.g. asm_Arm.dll) and creating a second DLL with the name of the original one (asmArm.dll) which, in turn , recalls the functions of the first one. This allowed attackers to inject their malicious code into the target controller.
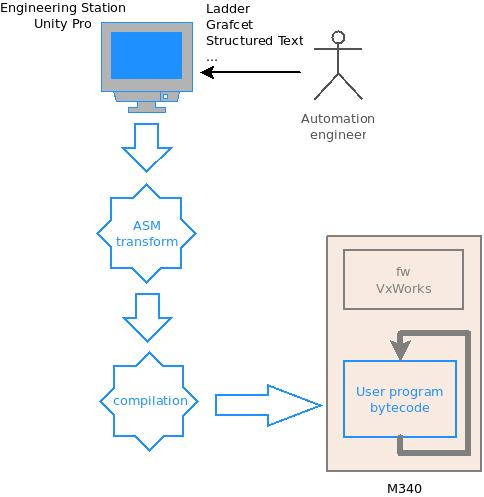
Airbus CyberSecurity researchers analyzed Schneider Electric’s Modicon M340 PLC to determine if it is vulnerable to similar attacks. The attack targeted the controller via Schneider EcoStruxure Control Expert engineering software, formerly known as Unity Pro.
Their analysis led to the discovery of a vulnerability that can be exploited to load malicious code onto Modicon M340 and M580 PLCs by replacing one of the DLL files associated with the engineering software, following the same pattern as Stuxnet.
“Such an attack could have serious consequences, including disruption of production processes or other types of damage,” said Airbus CyberSecurity.
“Even more interesting from an IT perspective, the attacker could turn the PLC into a proxy,” explained the Airbus researchers. “This would allow it to send requests and communicate with the network that the PLC is connected to. For example, it could access the internal corporate network to steal intellectual property or launch attacks to target other connected systems."
“The legitimate automation software would be running without showing any sign of the presence of a malicious program. The malware part periodically sends requests to a command and control server operated by the attacker via the Internet,” they explained.
How to lead the attack
While such an attack could be highly malicious or disruptive - or could give an advantage to the attacker - exploiting the vulnerability is no easy task. The attacker must first gain access to the target organization’s ICS perimeter and be able to communicate with the target PLC.
“This is already a very significant operation likely involving privileged access on a number of machines. If the attackers have reached this point, several security defense measures are either not in place or have failed,” noted the researchers at Airbus CyberSecurity.
The attacker must then download the automation program from the PLC. This can be done from a compromised engineering station or if the PLC is accessible to any machine on the network without authentication. The attacker must then recompile the automation program using the techniques described by the Airbus researchers and create a malicious program to embed into the legitimate automation software.
Finally, the attacker must upload the modified program to the PLC and execute it, but this requires stopping and starting the automation software, and experts say this could be noticed.
The solutions in place
The vulnerability discovered by Airbus researchers in Schneider Electric products is referred to as CVE-2020-7475 and classified as strict. It has been patched by the company with a hotfix for EcoStruxure Control Expert and firmware updates for Modicon M340 and M580 controllers as noted in this note.
Schneider Electric and Airbus encourage all customer companies to implement cybersecurity best practices across their operations in an effort to reduce the risk of attacks.
“Where necessary, this includes locating industrial systems and remotely accessible devices behind firewalls; installing physical controls to prevent unauthorized access; preventing access to mission-critical systems and devices from external networks; systematically patching security and activation of antivirus software; and the enforcement of whitelisting solutions,” Schneider said.
Important note
This article is intended for educational and informational purposes only. Any unauthorized action towards any control system present on a public or private network is illegal! The information contained in this and other articles are intended to make people understand how necessary it is to improve defense systems, and not to provide tools for attacking them. Violating a computer system is punishable by law and can cause serious damage to property and people, especially when it comes to ICS. All the tests that are illustrated in the tutorials have been carried out in isolated, safe, or manufacturer-authorized laboratories.
Stay safe, stay free.