5 minutes
Hacking: Profibus/Profinet
One of the challenges of pentesting in the OT/ICS environment is given by the protocols used which can also be very different from those of IT. ICS installations use a wide variety of protocols that they often share have little in common with standard Ethernet and TCP/IP.
This difference has been the strong point of OT installations for years, protecting them through the mechanism of “security by obscurity”. Now that these protocols are becoming more known and understood, security concerns in these facilities have been heightened.
In this article we see the main characteristics of one of these protocols: the Profibus.
The Profibus standard
Profibus (Process Fieldbus) is an open standard for industrial communication originally developed in Germany. It was started by a group of 21 companies and institutions called the “Central Association for Electrical Industry” (ZVEI), led by industrial giant Siemens. For this reason Profibus is widely used in Siemens products and is the communication bus exploited by the Stuxnet malware in the Iranian Natanz nuclear power plant during the famous cyber attack.
Profibus is an intelligent bi-directional multipoint protocol, where all Profibus devices are interoperable. The data can represent analog or digital values. It is a cheap, simple and high speed protocol. Profibus uses a two-wire connection for power and data.
The topology of the protocol is master-slave, like many other SCADA/ICS protocols, supporting master nodes through the use of token sharing. Similar to IBM’s token-ring protocol, only when the master has the token can it communicate with the slaves. The Profibus slave can only communicate with a master. The master Profibus node is typically a PLC or RTU and the slaves are sensors, motors or other control devices.
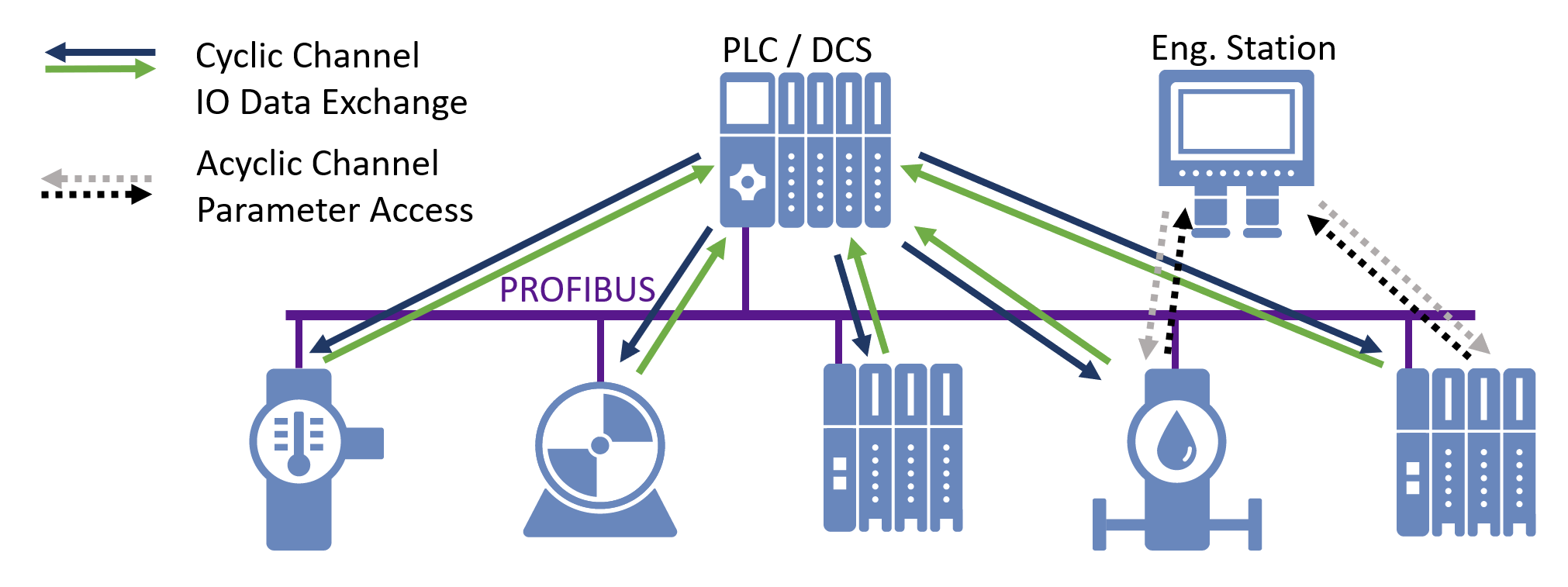
Profibus types
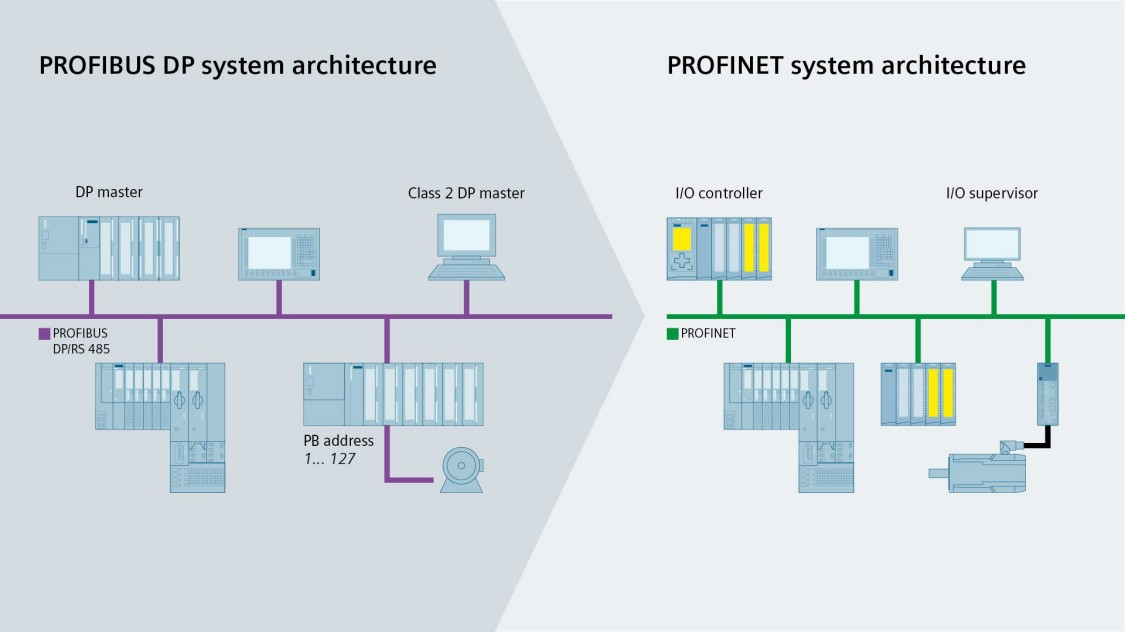
The Profibus protocol family is mainly divided into two categories: Profibus DP and ProfiNet. The uses change significantly: while the first is a traditional master-slave fieldbus with serial transmission with a ring network, the second is its evolution and allows communication between different bus segments using Ethernet.
Profibus FMS
This was the initial Profibus protocol. It was designed to communicate between PLC and PC. Unfortunately this simple protocol was not very flexible and consequently could not work in a more complex and complicated network. While still in use, the vast majority of Profibus networks use one of the newer versions.
Profibus DP (Decentralized Periphery)
Profibus DP is probably the most common of the Profibus protocols. It is easier and faster than the other types. It is available in three separate versions: DP-V0 (cyclic data exchange), DP-V1 (acyclic data exchange) and DP-V2 (isochronous slave-to-slave mode and data exchange) with each new version offering functionality additional.
Profibus PA (Process Automation)
Profibus PA, as the name suggests, was developed for Process Automation. This version of the protocol standardizes the process of transmitting measured data. It has also been designed for use in hazardous environments using Manchester Bus Powered (MBS) technology which uses lower power and therefore reduces the possibility of sparks and explosions.
PrifiNet (Process Field Net)
ProfiNet (Process Field Net) is another open standard for industrial automation designed for scalability. Instead of exchanging data using fieldbus (serial), it uses Ethernet (IEEE802.3) as the medium. It is included as part of IEC-61158 and IEC-61784. It initially used standard TCP/IP packets.
ProfiNet has the strength of providing data with tight time constraints. It uses IT standards such as TCP/IP and XML to communicate, configure and diagnose machines and devices. It can operate up to 100 Mbit/s over twisted pair or fiber optic cables.
ProfiNet is NOT Profibus over Ethernet, but they are compatible with using specific proxies to connect them.
ProfiNet has two classes of functions:
- ProfiNet I/O (input/output)
- ProfiNet CBA (Component Based Automation)
ProfiNet I/O
Connect distributed field devices and use real-time (RT) and standard (TCP/IP) communications.
The real-time channel (RT) is used for critical data that requires very short exchange times, such as cyclic process data, alarms and communication monitoring and is capable of executing 10 ms cycles.
The standard channel is used for configuration and parameter downloads, diagnostics, device management information, and other non-critical communications with exchange times in the 100ms range.
Still belonging to the I/O family, there is also the ProfiNet IRT (Isochronous Real-Time), which is used in drive systems with cycle times of less than 1 ms. Since ProfiNet IRT is a hardware based Layer 2 technology it is not routable.
Profibus I/O uses TCP/UDP port numbers 34962, 34963 and 34964.
ProfiNet CBA
It is designed for distributed industrial automation applications. ProfiNet CBA is based on the DCOM (Distributed Component Model) and RPC (Remote Procedure Call) standard. This also means that it then inherits its DCOM and RPC vulnerabilities.
ProfiNet CBA uses standard TCP port number 135.
The security of protocols
Like many OT/ICS protocols, Profibus DP also lacks authentication. This means that any node can spoof a master node. Since only the latter can control the slaves, this is one of the major vulnerabilities of the system. A forged master node would be able to acquire the token, disrupt the node’s functions and even cause a Denial of Service (DoS). Since most master nodes in a Profibus DP network are connected to an Ethernet network, this makes them susceptible to an Ethernet-based quasi-type of attack.
The same is true for ProfiNet. Since there are different technologies in this suite the risk depends on the one used. The exception, at least in part, is the ProfiNet IRT protocol which uses non-routable addresses and is therefore immune to IP vulnerabilities.
Important note
This article is intended for educational and informational purposes only. Any unauthorized action towards any control system present on a public or private network is illegal! The information contained in this and other articles are intended to make people understand how necessary it is to improve defense systems, and not to provide tools for attacking them. Violating a computer system is punishable by law and can cause serious damage to property and people, especially when it comes to ICS. All the tests that are illustrated in the tutorials have been carried out in isolated, safe, or manufacturer-authorized laboratories.
Stay safe, stay free.