2 minutes
Hacking: Metasploit SCADA modules
As penetration testers we have many resources at our disposal to test the security level of an IT system. One of the popular tools is Metasploit Framework, developed by Rapid7. It is a tool capable of covering the phases of enumeration, exploitation and privilege escalation, very flexible and modular.
For some time now, given the attention that the world of cybersec is dedicating to ICS infrastructures, we can find a long list of Metasploit modules that target SCADA systems, PLCs and the main industrial communication protocols.
And it is precisely due to the fact that ICS sites use different hardware and protocols that a very careful reconnaissance phase must be carried out in order to carry out a successful attack. You need to know the manufacturer and the protocol to find the appropriate module.
Below I have summarized the list of modules present at the time of writing this article, divided into auxiliaries (reconnaissance and commands) and exploitation ones.
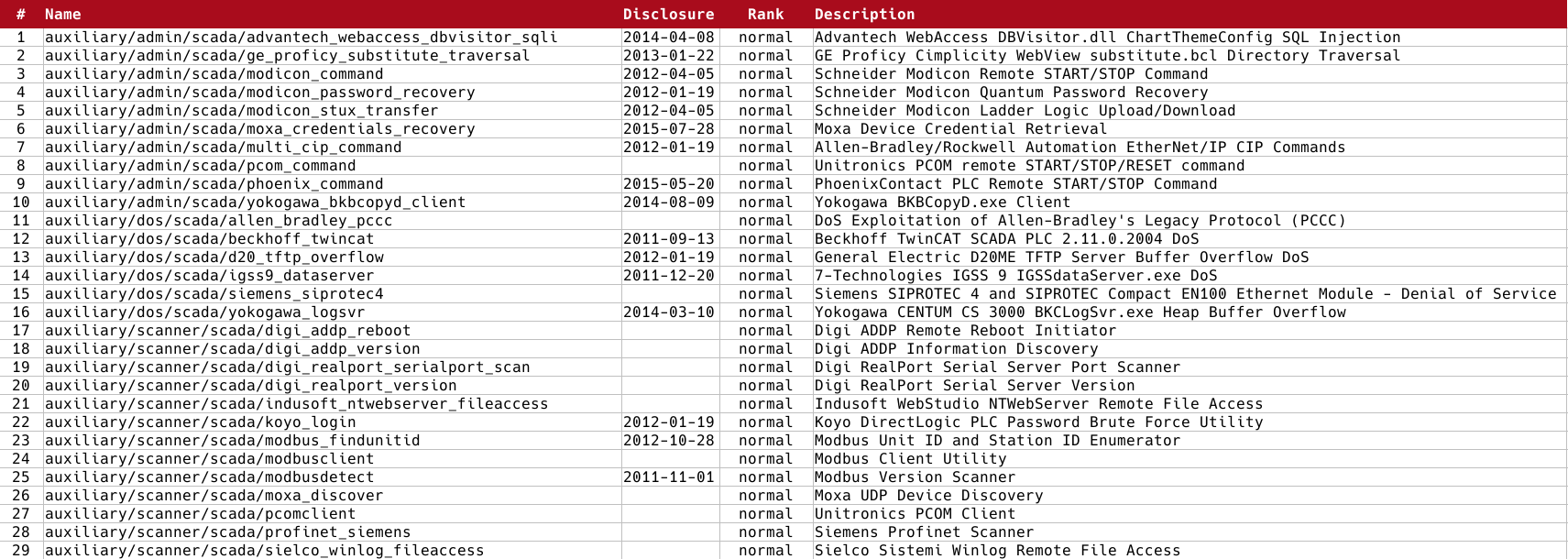
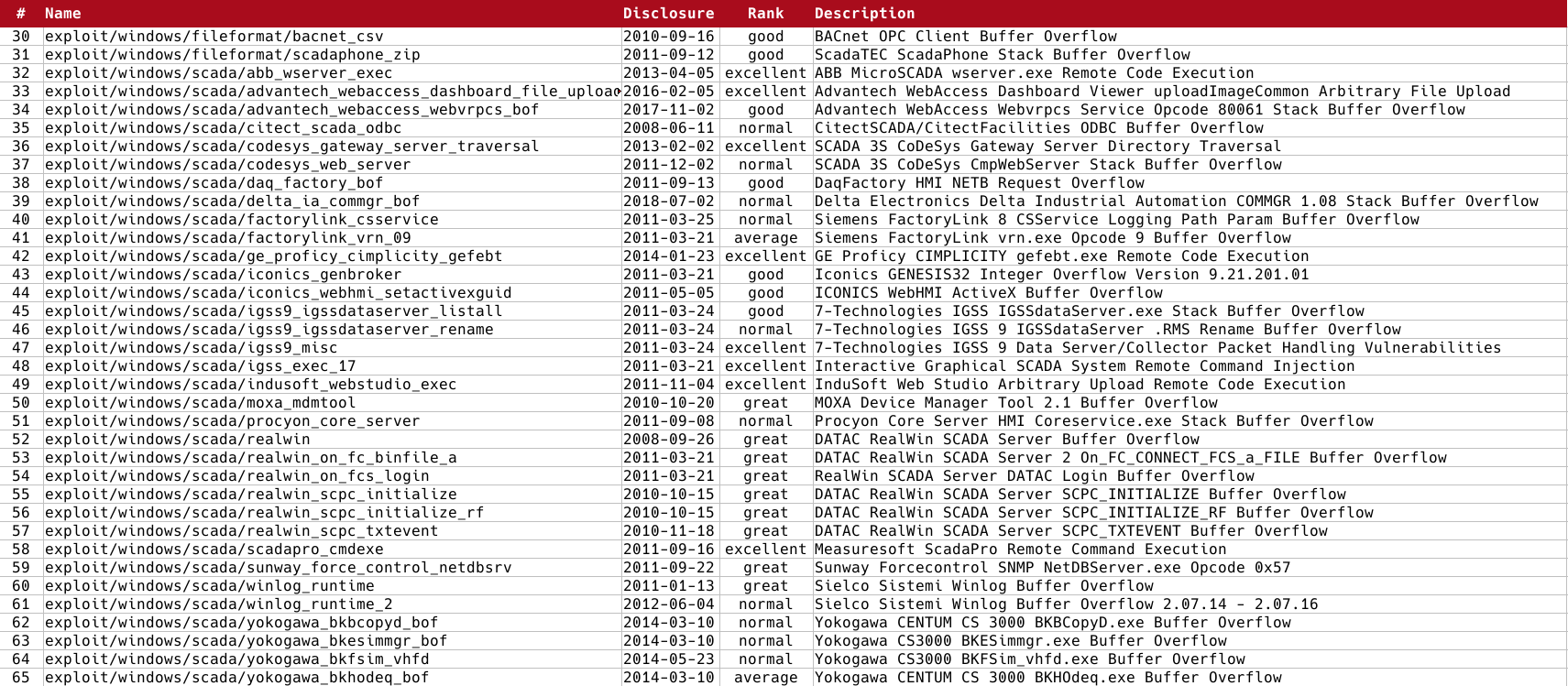
Important note
This article is intended for educational and informational purposes only. Any unauthorized action towards any control system present on a public or private network is illegal! The information contained in this and other articles are intended to make people understand how necessary it is to improve defense systems, and not to provide tools for attacking them. Violating a computer system is punishable by law and can cause serious damage to property and people, especially when it comes to ICS. All the tests that are illustrated in the tutorials have been carried out in isolated, safe, or manufacturer-authorized laboratories.
Stay safe, stay free.